MTG IoT – Key Management System
The MTG IoT Key Management System is designed to meet the specific needs of IoT device manufacturers and operators in all processes involved in managing key material.
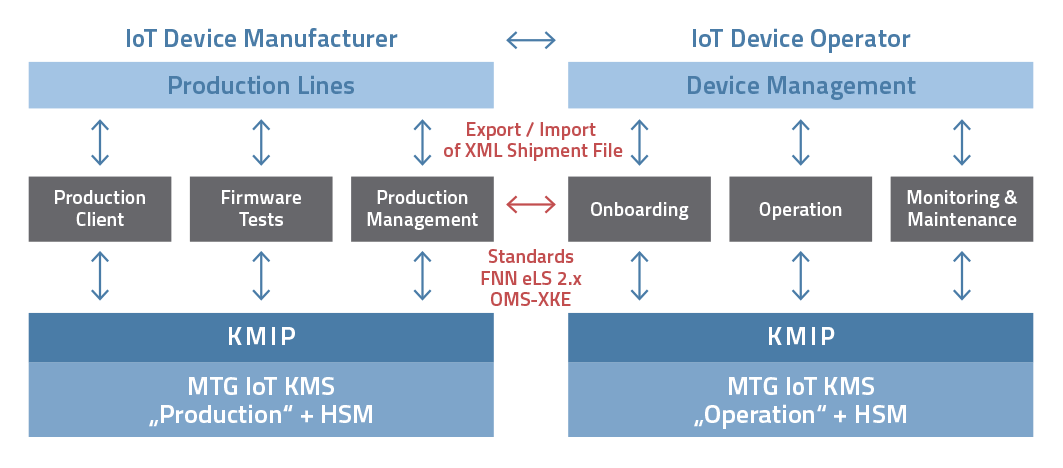
MTG IoT KMS from device production to operation (© MTG)
The MTG IoT KMS was designed to support the requirements of manufacturers and operators of IoT devices. The KMIP standard interface specifies all management operations for (e.g., digital certificates, private keys) that are stored and managed by a cryptographic key management system. A secure handover of the key material when sending the physical devices to the customer or between production sites will be managed with an electronic shipment file.
MTG Corporate PKI
In the Internet of Things, a large number of devices communicate with each other in network infrastructures. In order to protect these systems, no device may have access unless it has proven that it is trustworthy. The secure identity of a device is made particularly convenient and easy by relying on the MTG Corporate PKI.
The MTG Corporate PKI provides the necessary certificates for asymmetric encryption procedures and is and is designed to be optimally compatible with the MTG IoT KMS.
MTG Secure Boot Protector

Embedded system manufacturers should make sure that their devices boot only with original and unmodified firmware. MTG Secure Boot Protector utilizes digital signatures to ensure the authenticity of the embedded system throughout the lifecycle of the device and includes all boot, configuration and update processes.
Download & Links
Flyer MTG Key Management System
Flyer MTG Certificate Lifecycle Manager (MTG CLM)
Flyer MTG Managed Corporate PKI
Flyer MTG Secure Boot Protector
Video - MTG Secure Boot Protector - Live Demo
Use-Case: Iskraemeco to use MTG's cryptographic key management system
Flyer MTG ERS® - Enterprise Resource Security