Architecture
Cryptographic keys are the cornerstone of almost all security applications and protection mechanisms. It is essential that they are protected and used with the outmost care, so that all the infrastructures, services and business critical applications remain secure. The MTG KMS enables different applications in a company to access a remote, central security system that can perform all necessary crypto operations.

MTG Enterprise Key Management System Architecture (© MTG)
The MTG KMS architecture is part of the overall MTG ERS® system. This means that the system can be expanded with further important security components whenever required. This includes the MTG Certificate Lifecycle Manager, MTG Certificate Authority and the appropriate Hardware Security Module.
The targeted solutions which are based on KMS (e.g., BYOK, Code & Document Signing, Time Stamping, etc.) can be optimally accessed and managed via standard APIs (KMIP, PKCS#11, REST). The MTG KMS includes a specific Java SDK that provides a simple, user-friendly Java interface for easy client integrations. MTG-specific services and adapters are available for specific use cases, like IoT, Secure Boot or Smart Metering for example.
Features
MTG KMS manages the complete Key Management Lifecycle
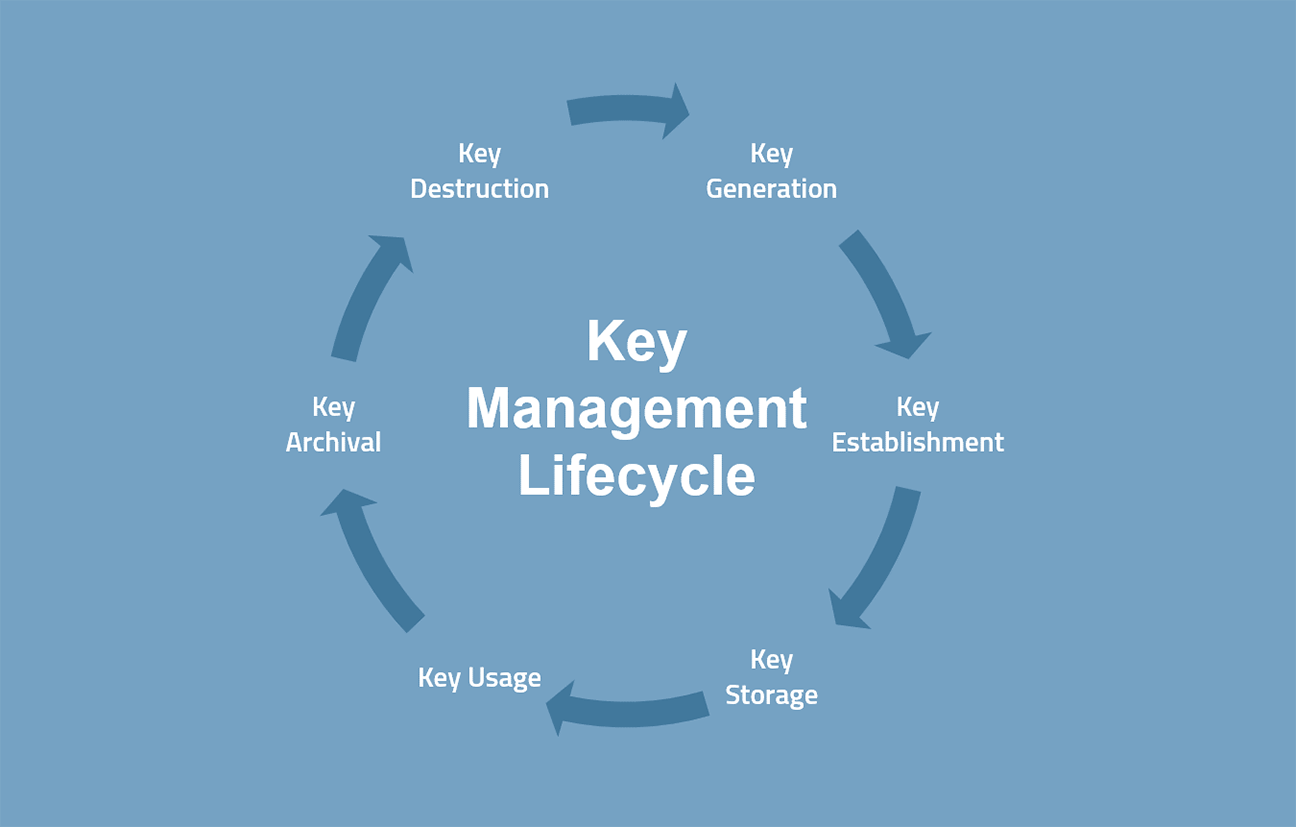
Key Management Lifecycle (© MTG AG)
Secure Key Storage
Central key storage is essential to keep control of all keys in a well-protected location. This prevents keys from being distributed nontransparent across the entire company.
-
Support for multiple on-premise and cloud Hardware Security Modules (HSM)
-
Utimaco
-
Entrust (nShield)
-
Thales (Luna)
-
- Support for database-stored, HSM-encrypted keys for better performance
- Support for key import and export through various formats
- Secure Key Generation for all modern cryptographic algorithms
- Support for Post-Quantum Cryptography
Secure Key Operations
- Support for all KMIP 2.x and PKCS11 operations
- Generic Cryptographic REST API that enables both simple and advanced cryptographic operations
- Symmetric & Asymmetric encryption
- Digital Signatures
- Hashing
- Random Number Generation
Key Lifecycle Management
- Support for Key Expiration Dates
- Support for multiple business domains
- Secure Key Archival & Destruction
- Strict cryptographic policy enforcement about allowed algorithms and parameters for different use cases
- Enterprise Roles & Rights System
Key Management
Interoperability Protocol
The OASIS Standard Key Management Interoperability Protocol (KMIP) was developed as an interoperable protocol that defines the standard communication between key management servers and clients.
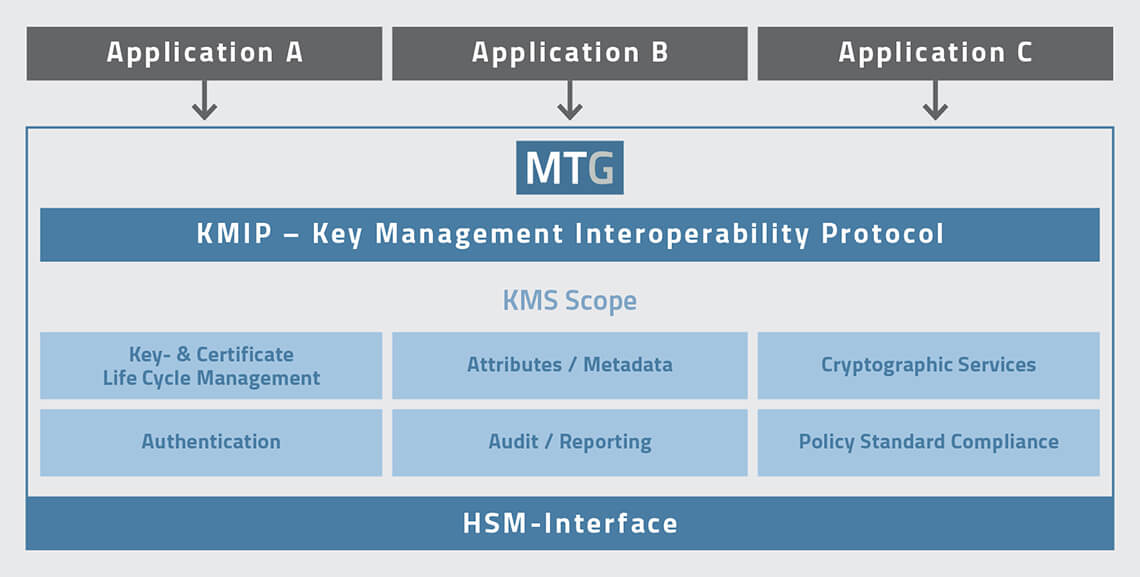
MTG KMS already supports all cryptographic functions from the KMIP standard (© MTG AG)
KMIP specifies all management operations for objects (e.g., digital certificates, private keys) stored and managed by a cryptographic key management system. The KMIP standard includes operations for symmetric and asymmetric cryptographic keys, digital certificates and templates that simplify the creation and control the usage of objects.
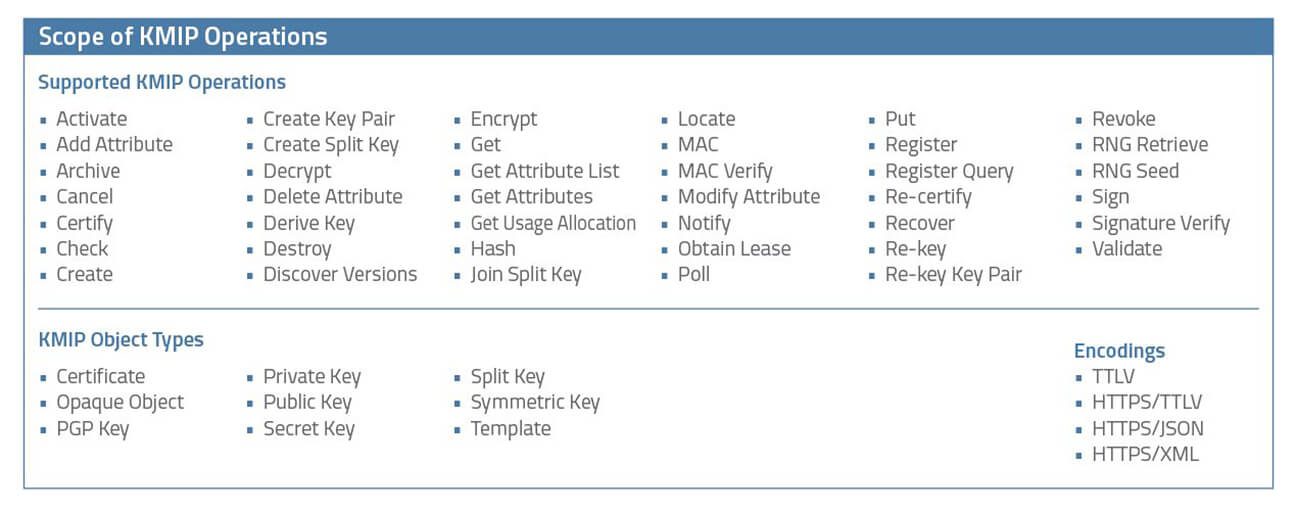
KMIP has already been implemented by leading companies (e.g. Dell, HP, IBM, Oracle, SafeNet) and is specifically supported in the Internet of Things (IoT). The KMS services (microservices) and adapters from MTG that are plugged in above the KMIP interface simplify the connection of the applications even further.