Need of a Secure Firmware
Manufacturers of embedded systems should ensure that their devices only start with original and unmodified firmware and that only authorized configuration files and updates can be used. The original software may run on counterfeit hardware or, vice versa, counterfeit or manipulated software may run on the original hardware.
The challenge here is to protect the system in such a way that malicious code is detected by the secure boot mechanism and is not executed. Only an authentic bootloader and operating system will be booted in combination with an authentic file system. Vulnerabilities can be fixed in a regular secure update process. Thus, the system always remains trustworthy. Manufacturers of IoT devices from various industries are increasingly facing the task of protecting their systems in this way.
When implementing a secure boot process, there are high requirements for the IT security and there is no room for compromise. This can be achieved with the help of code signatures, which ensure the origin of the firmware from a trusted source by verifying the signature during the boot process. The required secret key material must be stored in a highly protected environment at the enterprise and only authorized users should have access to it. There may be several secret keys for different products or product lines which need to be managed. If this is not implemented consistently and end-to-end, there is a high risk of manipulation and misuse.
MTG Secure Boot Protector enables the secure life cycle management of digital certificates and secret keys needed for the secure boot management process.
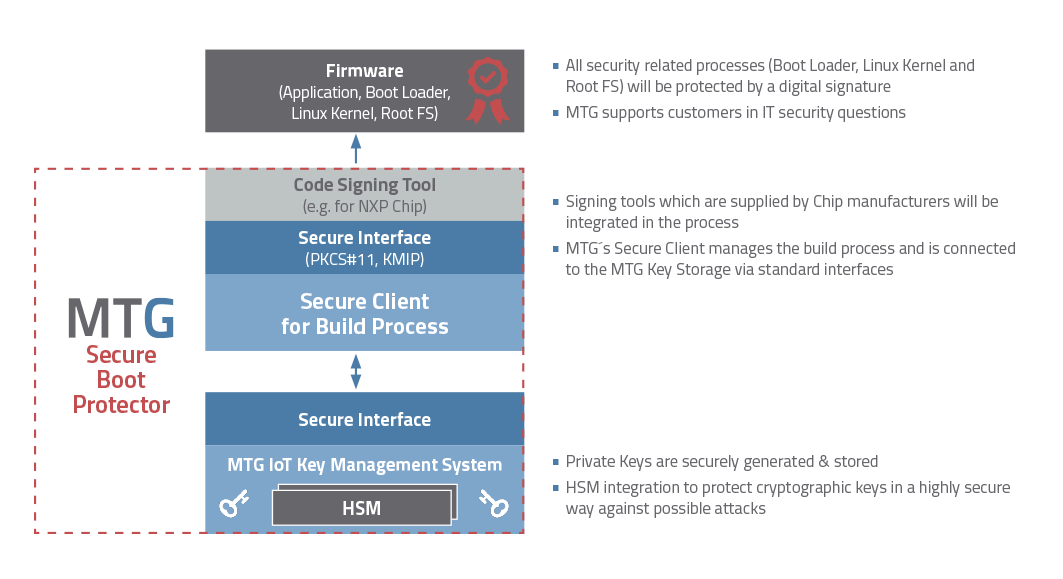
MTG Secure Boot Protector (© MTG AG)
Secure Boot Protector
When an embedded device boots, it executes programs that are stored in its memory. If the code is not legitimate or incorrect this device will mal-function or endanger the infrastructure in which it is located. Therefore, booting of the device is a critical operation and needs to be secured to ensure that a device executes only legitimate software. During production the firmware needs to be protected by a signature with a private key. This makes sure that only the original firmware of the product is used.
MTG Secure Boot is responsible for all crypto operations (encryption, signing, key generation…), which are needed for secure boot, configuration and update of embedded systems. It covers all needed elements to fully protect the firmware:
- Boot process
- Update process
- Protection of secret keys
- Protection of bootloader and operating system
- Encryption of the executed code (e.g., bootloader or Linux Kernel)
The Integration of all necessary processes is very simple thanks to the MTG IoT Key Management system. This also avoids complex configuration tasks when using hardware security modules. The solution can be shared centrally for different embedded devices using different chip manufacturers. This simplifies reliably the management of all necessary processes. The integration of a PKI for the variable generation of X.509 certificates is possible. Different CA hierarchies (Root CA, Sub CA) and signature algorithms are supported.
Easy Deployment
MTG Secure Boot Protector can be quickly and easily put into operation at a central and secure location. The connection of the development and production environment can be implemented very flexibly. All signing tools supporting PKCS#11 can be integrated directly. Code signing tools of the chip manufacturers (e.g., NXP’s HABv4) are integrated into the system according to customer requirements. MTG provides support for all IT security relevant questions regarding the configuration of the firmware. The optional Hardware Security Modules are pre-configured and provided on a fail-safe basis.


